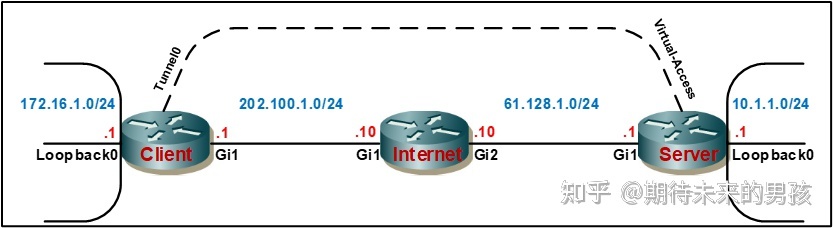
¶ client
!
aaa new-model
!
aaa authentication login noacs none
aaa authorization network Qytang-Local-Group-Author-List local
!
redundancy
!
crypto ikev2 authorization policy Qytang-IKEv2-Author-Policy
!
crypto ikev2 keyring Qytang-IKEv2-Keyring
peer server
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco
pre-shared-key remote cisco
!
crypto ikev2 profile Qytang-IKEv2-Profile
match identity remote address 0.0.0.0
identity local email spoke@qytang.com
authentication remote pre-share
authentication local pre-share
keyring local Qytang-IKEv2-Keyring
aaa authorization group psk list Qytang-Local-Group-Author-List Qytang-IKEv2-Author-Polciy
!
crypto ikev2 client flexvpn QYtang-Flex-Client
peer 1 61.128.1.1
client connect Tunnel0
!
!
crypto ipsec profile Qytang-IPSec-Profile
set ikev2-profile Qytang-IKEv2-Profile
!
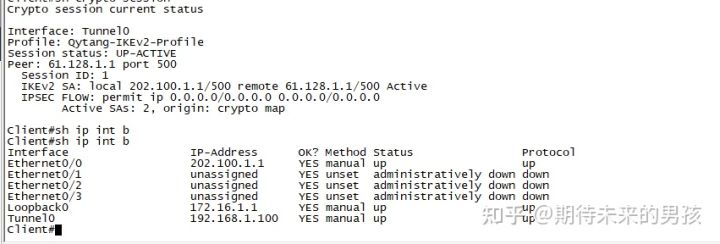
interface Loopback0
ip address 172.16.1.1 255.255.255.0
ip ospf 1 area 0
!
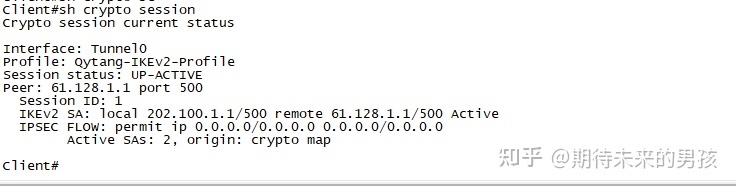
interface Tunnel0
ip address negotiated
ip mtu 1400
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile Qytang-IPSec-Profile
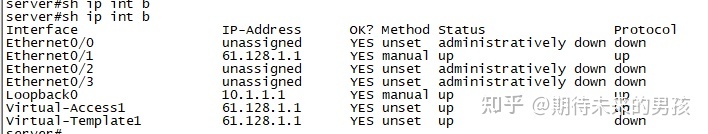
¶ Server
aaa new-model
!
!
aaa authentication login noacs none
aaa authorization network Qytang-Local-Group-Author-List local
!
crypto ikev2 authorization policy Qytang-IKEv2-Author-Policy
pool Qytang-Address-Pool
!
crypto ikev2 keyring Qytang-IKEv2-Keyring
peer Flex-VPN
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco
pre-shared-key remote cisco
!
peer Spoke
identity email spoke@qytang.com
pre-shared-key cisco
!
!
!
crypto ikev2 profile Qytang-IKEv2-Profile
match identity remote address 0.0.0.0
match identity remote email domain qytang.com
authentication remote pre-share
authentication local pre-share
keyring local Qytang-IKEv2-Keyring
aaa authorization group psk list Qytang-Local-Group-Author-List Qytang-IKEv2-Author-Policy
virtual-template 1
!
crypto ipsec profile Qytang-IPSec-Profile
set ikev2-profile Qytang-IKEv2-Profile
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
ip ospf 1 area 0
!
interface Virtual-Template1 type tunnel
ip unnumbered Ethernet0/1
ip mtu 1400
ip ospf 1 area 0
tunnel mode ipsec ipv4
tunnel protection ipsec profile Qytang-IPSec-Profile
!
router ospf 1
router-id 1.1.1.1
!
ip local pool Qytang-Address-Pool 192.168.1.100 192.168.1.200
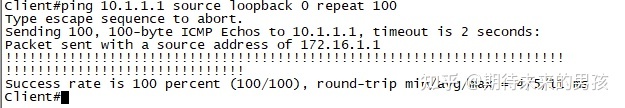
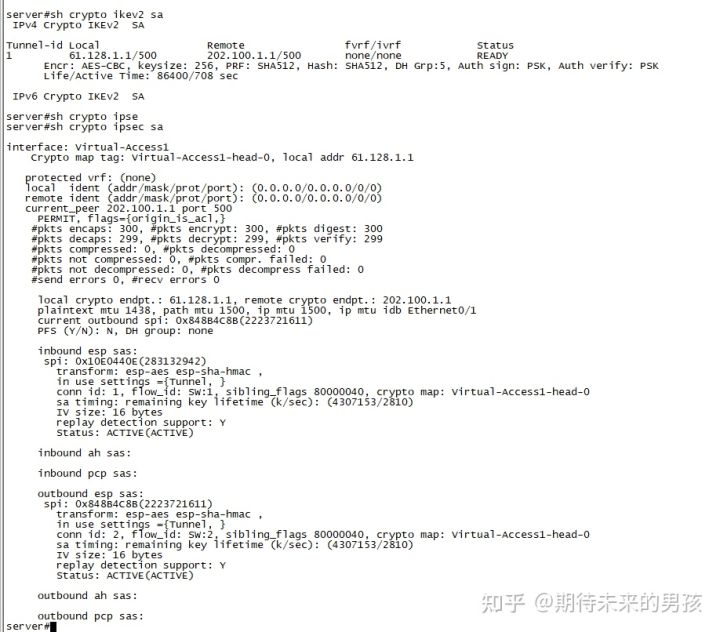
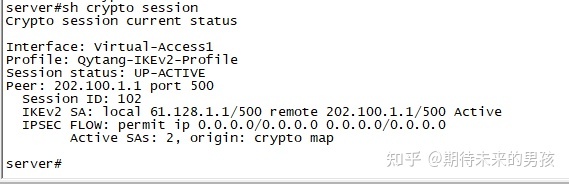
¶ 测试
¶ 排错
*Jan 13 08:35:02.668: IKEv2:Using mlist Qytang-Local-Group-Author-Lis and username Qytang-IKEv2-Author-Policy for group author request *Jan 13 08:35:02.668: IKEv2:AAA group author request failed *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 0,SA ID = 1):AAA group authorization failed
*Jan 13 08:35:02.668: IKEv2:(SESSION ID = 0,SA ID = 1): *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Verification of peer’s authentication data FAILED *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Sending authentication failure notify *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Building packet for encryption. Payload contents: NOTIFY(AUTHENTICATION_FAILED)
server# *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Sending Packet [To 202.100.1.1:500/From 61.128.1.1:500/VRF i0:f0] Initiator SPI : 263F99FAD001A16C - Responder SPI : 5352741A4CF5ECB0 Message id: 1 IKEv2 IKE_AUTH Exchange RESPONSE Payload contents: ENCR
*Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Auth exchange failed *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):: Auth exchange failed *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Abort exchange *Jan 13 08:35:02.668: IKEv2:(SESSION ID = 76,SA ID = 1):Deleting SA server#
由于3A名称写错导致认证无法通过 ikev2 无法建立 Qytang-Local-Group-Author-Lis