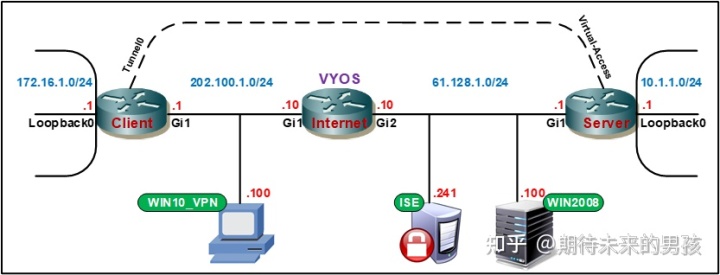
hostname Server
!
enable password cisco
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet1
ip address 61.128.1.1 255.255.255.0
no shu
!
ip route 0.0.0.0 0.0.0.0 61.128.1.10
!
===================================================
ip name-server 61.128.1.100
ip domain name qytang.com
ip domain-lookup
!
crypto key generate rsa label Server.qytang.com modulus 1024
!
crypto pki trustpoint CA
enrollment terminal
fqdn Server.qytang.com
subject-name cn=Server.qytang.com,ou=qytang
revocation-check none
rsakeypair Server.qytang.com 1024
eku request server-auth
!
aaa new-model
!
aaa authentication login noacs none
aaa authorization network Lxf-Local-Grp-Auth-List local
!
line con 0
login authentication noacs
!
ip access-list standard Server-Network
permit 10.1.1.0 0.0.0.255
!
ip local pool Lxf-Address-Pool 192.168.1.100 192.168.1.200
!
crypto ikev2 authorization policy Lxf-IKEv2-Author-Policy
pool Lxf-Address-Pool
route set access-list Server-Network
===========================================================
!
crypto pki certificate map Lxf-Cert-Map 10
subject-name co ou = hardwareclient
!
crypto ikev2 profile Lxf-IKEv2-Profile
match certificate Lxf-Cert-Map
identity local fqdn Server.qytang.com
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
aaa authorization group cert list Lxf-Local-Grp-Auth-List Lxf-IKEv2-Author-Policy
virtual-template 1
!
crypto ipsec profile Lxf-IPSec-Profile
set ikev2-profile Lxf-IKEv2-Profile
!
interface Virtual-Template1 type tunnel
ip unnumbered GigabitEthernet1
tunnel mode ipsec ipv4
tunnel protection ipsec profile Lxf-IPSec-Profile
------------------------------------------------------------------------------
hostname Client
!
enable password cisco
!
interface GigabitEthernet1
ip address 202.100.1.1 255.255.255.0
no shu
!
interface Loopback0
ip address 172.16.1.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 202.100.1.10
!
===================================================
ip name-server 61.128.1.100
ip domain name qytang.com
ip domain-lookup
!
crypto key generate rsa label Client.qytang.com modulus 1024
!
crypto pki trustpoint CA
enrollment terminal
fqdn Client.qytang.com
subject-name cn=Client.qytang.com,ou=HardwareClient
revocation-check none
rsakeypair Client.qytang.com 1024
eku request client-auth
!
===========================================================
aaa new-model
!
aaa authentication login noacs none
aaa authorization network Lxf-Local-Grp-Auth-List local
!
line con 0
login authentication noacs
!
ip access-list standard Client-Network
permit 172.16.1.0 0.0.0.255
!
crypto ikev2 authorization policy Lxf-IKEv2-Author-Policy
route set access-list Client-Network
===========================================================
crypto pki certificate map Lxf-Cert-Map 10
subject-name co ou = qytang
!
crypto ikev2 profile Lxf-IKEv2-Profile
match certificate Lxf-Cert-Map
identity local fqdn CLient.qytang.com
authentication remote rsa-sig
authentication local rsa-sig
aaa authorization group cert list Lxf-Local-Grp-Auth-List Lxf-IKEv2-Author-Policy
pki trustpoint CA
!
crypto ipsec profile Lxf-IPSec-Profile
set ikev2-profile Lxf-IKEv2-Profile
!
!
interface Tunnel0
ip address negotiated
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile Lxf-IPSec-Profile
!
crypto ikev2 client flexvpn Lxf-Flex-Client
peer 1 61.128.1.1
client connect Tunnel0
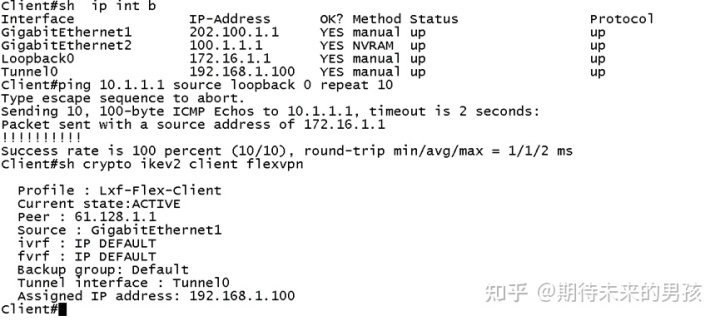
验证
申请证书
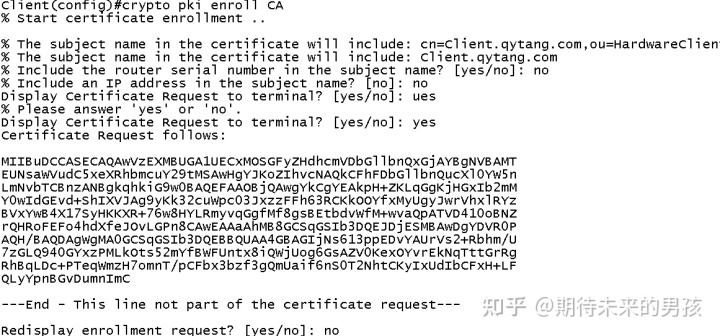
导入证书
根证书