¶ 一、穿越防火墙
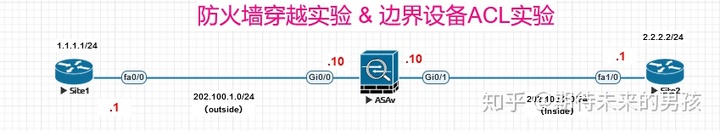
Site2#ping 1.1.1.1 source 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
.....
Success rate is 0 percent (0/5)
Site2#sh crypto isakmp sa de
IPv4 Crypto ISAKMP SA
dst src state conn-id status
202.100.1.1 202.100.2.1 QM\_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
Site2#sh crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 0 0 202.100.2.1
2 IPsec DES+MD5 9 0 0 202.100.2.1
1001 IKE SHA+DES 0 0 0 202.100.2.1
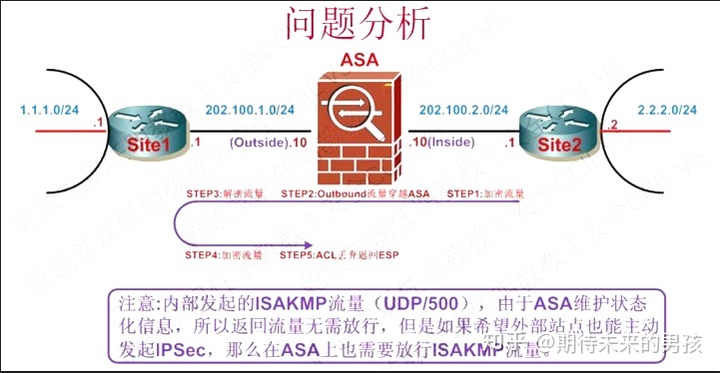
¶ 解决方法:
access-list out extended permit udp host 202.100.1.1 eq isakmp host 202.100.2.1
#允许从外发发起ipsec 连接
access-list out extended permit esp host 202.100.1.1 host 202.100.2.1
#放行esp流量
access-group out in interface Outside
中间设备需要放行流量
1.加密点之间的ISAKMP流量(UPD500)
2.加密点之间的ESP或者AH流量
¶ 二、IPSec流量放行问题
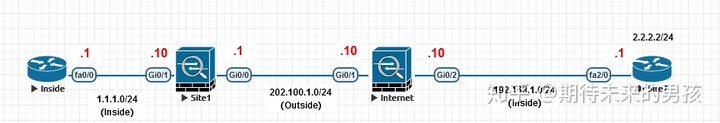
IOS12.3之后 对与VPN 解密后的明文流量由 crypto map acl 来控制
access-list 110 permit tcp host 1.1.1.1 host 2.2.2.2 eq telnet
crypto map cisco 10 ipsec-isakmp
set ip access-group 110 in
并且使用 crypto map acl 后 需重新建立ipsec SA 才能生效,删除 crypto map acl 不需要重新建立ipsec SA
Inside#telnet 2.2.2.2
Trying 2.2.2.2 ... Open
Password required, but none set
\[Connection to 2.2.2.2 closed by foreign host\]
Inside#ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
¶ 三、NAT-T穿越的问题


¶ 故障排除:
show run | s crypto //查看VPN所有配置
show ip access
show crypto isakmp**sa**//查看第一阶段**sa**
show crypto**ipsecsa**//查看第二阶段**sa**
clear crypto sa//清除邻居关系
clear crypto isakamp//清除邻居关系
debug crypto isakmp //查看第一阶段令居建立过程
debug crypto **ipsec**// 查看第一阶段令居建立过程